Cyber security architect – To protect a business from cyberattacks, an organization needs a cyber-security architecture that includes security software and appliance solutions. Furthermore, as organizations embark on digital transformation projects and extend IT services beyond the traditional network perimeter, a flexible cyber security architecture is required. Finally, a Zero Trust security architecture is necessary because cyber dangers occur within and outside the security perimeter.
As a result, they serve as the primary point of contact for all matters about cybersecurity.
Cyber Security Architect Career Guide
Even if you don’t want to know about it, you’re constantly bombarded with headlines about corporate cybersecurity breaches and phishing scams. However, cybercrime has been a major issue in recent years, highlighting the need for strong cybersecurity measures.
Regardless of whether they’re a business, government institution, or private citizen, everyone wants their personal information safe. As a result, our personal information, financial transactions, and day-to-day activities are all conducted online.
Security architects are an important part of the puzzle. Understanding what cybersecurity architecture is and why it’s important to become one is the goal of this article. Find out why this is an excellent career choice by reading on.
What does a Cyber Security Architect do?
Security architects conduct assessments of their organizations’ IT and computer systems to discover strengths and flaws. On local and wide area networks and a virtual private network, risk assessments and ethical hacks are performed. In addition, they evaluate the effectiveness and efficiency of routers, firewalls, and other comparable systems.
Architects of security think like criminals. They test the limitations of current computer and network security mechanisms. Security architects propose and implement architectural modifications to improve security in existing systems.
It is not uncommon for these experts to design and implement new security architectures from scratch. In addition, organizational policies and industry standards are incorporated into their understanding of security hardware and software, organizational needs, and cybersecurity threats.
They must create budgets for the security systems and networks they design, maintain, and manage, and track spending and allocate resources as needed. Security architects intent to guide information technology (IT) security team members. IT analysts and security administrators are also in charge of coordinating effective security measures under the leadership of the security engineers.
When a security breach occurs, security architects are called in to help. Security architects investigate occurrences and prepare detailed reports for their coworkers, managers, and executives when they occur. In addition, they make necessary adjustments, updates, and upgrades in response to security threats and breaches.
Cyber Security Architect Roles and Responsibilities
- Understanding the organization’s technological and informational infrastructure from top to bottom
- Security architectures for all IT projects should be planned, researched, and designed to be trustworthy, powerful, and flexible.
- Conducting risk evaluations and security assessments on the completed infrastructure.
- New security standards, technologies, and authentication methods are being investigated.
- Ensure that all workers adhere to all necessary corporate security policies and procedures and ensure that the policies and processes are properly implemented and maintained.
- Networking devices, such as routers, virtual private networks (VPN), local area networks (LANs), wide area networks (WANS), firewalls, and any other network devices.
- Authorizing all firewalls, VPNs, routers, servers, and IDS scanning technologies.
- Establishing a budget for all cybersecurity measures and assessing any potential integration concerns
- Building important public infrastructures, such as digital certificates and certification authority (PKI) (CA)
- To ensure that the organization’s final security measures are working as expected,
- Guiding and supervising security teams in their technical endeavors
- Assuming responsibility for all initiatives and training efforts aimed at increasing security awareness among non-IT personnel
- After a security-related incident occurs, offer a thorough post-event study to ensure that the problem is not re-occurring in the future.
- Keeping the organization’s security systems up-to-date
Not every company or organization will require a cybersecurity architect to perform all of these functions. However, other firms may demand more from their architects.
Qualifications and criteria for the position of Cyber Security Architect
According to CSOonline, an information security architect’s job description includes a detailed breakdown of the abilities and competencies needed to succeed. The following are some of the most important requirements:
Experience
- With the help of an information security team to create and execute security solutions, new technologies can be used to monitor and improve those solutions.
- Assist businesses, customers, and regulators with their security demands by creating and implementing best practices and security standards.
- Cloud computing security issues include data breaches, hacking, account hijacking, malevolent insiders, third parties, authentication, APTs, data loss, and DDoS attacks.
- Management of user identities and access to critical technical resources and information assets
General knowledge
- Excellent verbal and written communication skills; good analytical and critical thinking abilities.
- Strong leadership, project management, and team-building abilities are required, and the ability to lead teams and drive initiatives across several departments.
- The ability to identify hazards, incorporate processes, operations, technological initiatives, and information security programs has been demonstrated.
- Effectiveness as a subject matter expert who can communicate complicated concepts to individuals with little or no technical knowledge.
The ability to perform a task with a high degree of accuracy:
- Windows, UNIX, and Linux are all examples of operating systems.
- Web services, APIs, scripting languages, and a relational database management system (RDBMS) like MS SQL Server or Oracle are all technologies used to build web applications.
- Understanding key industry standards and procedures, such as ISO27001 and the National Institute of Standards and Technology.
- To combat corporate fraud, the Treadway Commission’s Committee of Sponsoring Organizations (COSO) and the Control Objectives for Information and Related Technologies (COBIT) have teamed up.
- An information security management system that meets the requirements of ISO 27001
- Security measures for routers, switches, and VLANs; wireless security.
- Methodology for assessing risk, policy development, role-based authorization methodologies, authentication technologies, and security attack types
How to become a Cyber Security Architect?
To become a cybersecurity architect, you’ll need to put in the time and effort. This is a high-paying, high-potential career, but you’ll need to work there. The good news is that we’ll walk you through the process!
Step 1: Choosing a Career path
To become a cyber-security architect, the first step is to figure out whether or not this is the career path for you. Cyber security is a highly specialized field that requires a wide range of technical and non-technical abilities. However, you’ve got the technical abilities first because they’re the hardest to learn.
Many people who work in cyber security do so because they have a natural aptitude for logic puzzles, mathematics, and computers. To succeed as a cyber-security architect, you must be able to self-teach yourself programming and have excellent grades in math and science classes. Your passion for solving challenges and an obsessive focus on every byte of code will also be required.
Step 2: Learning Cyber Security Related topics
There is a second step after you’ve decided that cyber security is the career route for you. Learning more about the issue is the next logical step. Reading books on cybersecurity-related ethical hacking and computer programming is good to start. Other unstructured web resources, such as blogs may pique your curiosity.
For those who want a degree or a certification in security, this is an option to consider. Since academic credentials are regarded greatly, a degree is generally the best option. A two-year associate degree in cyber security is an option if you’re in a hurry. If your local community college does not offer a degree in Information Security, check to see if they offer a degree in computer science or information technology.
Additionally, you can search for certifications on the internet and other locations. High-tech courses are offered in schools and institutes, with many of them focusing on certification. When you go through this method, you’ll be able to zero in on what interests you most. Verifiable credentials, such as certifications in penetration testing or malware exfiltration, can be obtained in addition to finishing a college course.
Step 3: Pursuing a Bachelor’s Degree
The third step is to look for a recognized program before pursuing a bachelor’s degree in cyber security or computer science. In addition to CHEA-approved regional accreditation, you should look for a program with ABET or CAE designations. For example, engineering schools are accredited by the Accreditation Board for Engineering and Technology. In addition to this, they evaluate and accredit departments of computer science, cyber defense, and information technology.
CAE is a credential, unlike the CAE, which focuses only on cyber security. The National Security Agency and the Department of Homeland Security collaborated to create the CAE. Given the increasing number of cyber-attacks, their mission is to produce high-quality cyber security specialists. The CAE has approved various cyber security degree programs, including associate’s, bachelor’s, and master’s degree options.
Step 4: College Degree in Cyber Security
Consider an internship or other work experience as you pursue certifications or a college degree in cyber security. An internship is probably preferable for students who are enrolled full-time. Internship opportunities in cyber security can be found in large corporations, consulting firms, and smaller businesses. Federal law enforcement internships and fellowships go; they’re the best.
As a non-academic, non-formal learner, you may be able to secure an internship, but it may be more difficult for you to do so. However, you can begin working in an IT department with security analysts and other IT professionals who may act as mentors shortly. Put another way; it’s possible to work as a temporary IT employee and then spend short periods in various IT environments. In addition, it is possible to take time off between assignments to gain new qualifications if you keep your spending in check.
What is the skill required to become Cyber Security Architect?
Accreditation is critical to the cybersecurity business because it teaches new skills, allows IT professionals, to expand their knowledge, and certifies their competence to potential employers.
In the field of cybersecurity, some of the most prestigious certificates include:
- Certified Information Systems Security Professional – Information Systems Security Architecture Professional (CISSP-ISSAP)
- Certified Information Systems Security Professional (CISSP)
- Certified Information Security Manager (CISM)
- Certified Information Systems Auditor (CISA)
Most organizations demand security architects have at least a bachelor’s degree. However, according to the CSOonline job description, “a master’s in cybersecurity is an even bigger benefit” if you have a master’s in an IT field.
To address the growing demand for security architects and other cybersecurity experts, more colleges and universities are now providing bachelor’s and master’s degree programs — both on-campus and online.
What is Cyber Security Architect Salary 2022?
Cybersecurity as a career may be on your mind at this point. For example, what is the average income for a cybersecurity architect? Is there a lot of demand for cybersecurity architects? What are the advantages and perks?
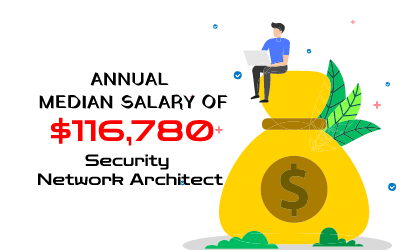
According to Payscale, the average compensation for a cybersecurity architect is USD 122,634. Although this may vary depending on where you live, how many years you’ve worked in the field, and your relevant talents. Incentives, profit-sharing, and generous health benefits may also be available to a cybersecurity architect.
Security Architect:
- Average salary $121,600
- Pay range $84,000–$156,000
Senior Security Architect:
- Average salary $144,716
- Pay range $113,000–$170,000
For those concerned about demand, the Indeed blog offers some good news.
First, it’s no surprise that the demand for cybersecurity architects is rising, given that CEOs in the United States place cybersecurity as their top priority. In addition, the recent spate of high-profile cybercrime instances has led to a surge in cybercrime fears.
According to the Bureau of Labor Statistics, cybersecurity employment is expected to expand by 37 percent between 2012 and 2022. However, as baby boomers retire and millennials don’t replace them at the same rate, there appears to be a widening skills gap in the profession.
Cybersecurity architects are in great demand because we live in a society that increasingly conducts business and leisure activities online. However, you’ll need the right abilities and training to write your ticket in this field.









Leave a Reply